

How To Turn On Internal Mobile Hotspot for Windows 10? One of them being the ability to create a Wi-Fi hotspot. The great benefit here is...
How can you permanently delete files without sending them to the recycle bin? If you are a Windows user, chances are that you always have to deal...

How To Hibernate your computer in Ubuntu? The great thing is that Ubuntu is extremely powerful and at the same time it integrates some rather impressive...

How To Find Saved Wi-Fi Passwords In Linux? The cool thing here is that you just have to add a few commands and you are ready to...

Windows Update Is Stuck In Windows 10 what can you do? Whether you like it or not, this is something that can and may happen. What you...

Kali Linux tips to consider after installation. With that in mind, here are some of the best things you can do to optimize it after its installation....

Top Youtube channels to Learn Ethical Hacking in 2017. So, you decided to become an ethical hacker and looking for free resources online? There are many...


Great youtube channels to follow in Computer science tutorials. Some interesting youtube channels to follow to get started in computer science. Khan Academy >_ link CS50 >_link...

The idea is that dual booting can make things a reality here, so it’s up to you to make the right pick and opt for the...
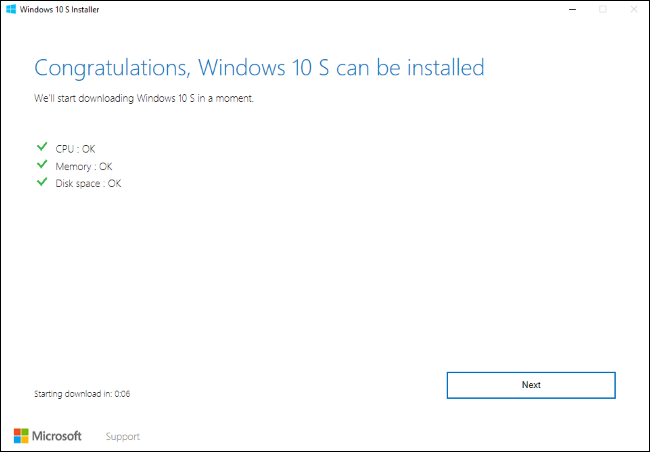

Windows 10 S is a new Windows variant designed to bring in front a dedicated set of features for some specific Windows devices. You can install...