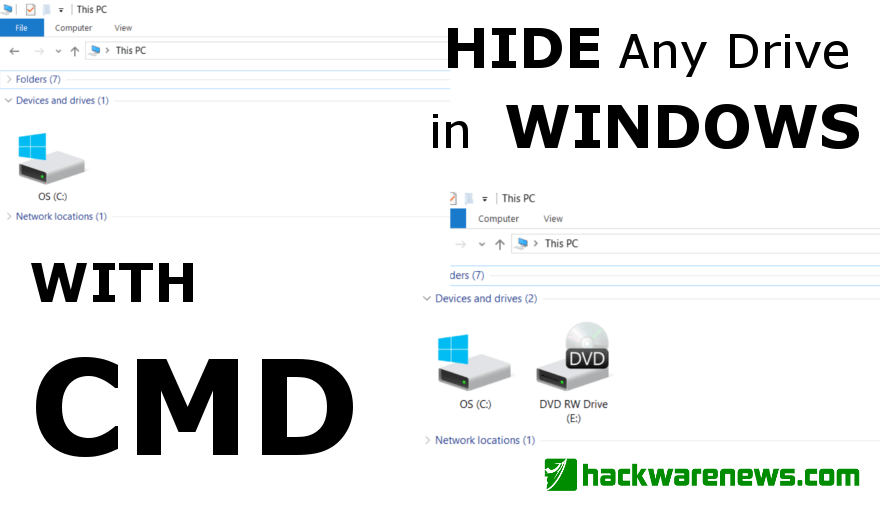
Hide Any Drive in Windows Using Command Prompt. Windows CMD is powerful tool to achieve some tasks that normally cannot be done without a third-party software/tools....

2018 is not going to be hack-free, so make your New Year Resolution here with "to-do lists” from Hackwarenews!

Google search in Linux CLI. Making a google search in Linux via CLI is not a just a geek thing anymore, as Linux gaining popularity among normal...

What are Top 10 Common Hacking Techniques? We don’t need to explain why it is important to know what are the commonly used hacking techniques. Below is...
Port scanning or OS fingerprinting. Believe it or not! The fact is pretty obvious that footprinting is essential to any successful attack. By and large, 70% of...


Fundamentals of Ethical Hacking. Footprinting is understood as information gathering and very first step in any cyber-attack on information systems. It is somewhat crucial for the...

Pen Testing Tools The Pros Use. What is pen testing? Penetration testing is a test performed by professional hackers to determine if a system is vulnerable...