

3 Reasons To Kickstart A Career As An Ethical Hacker. It’s a techie dream job to spend your day trying to hack into systems and networks,...

This 6-course bundle comprises of a huge 262 lessons and hours and hours of content that will help push you to the next level of your...

In this Quick Look, we are going to be looking at Pay What You Want: The Machine Learning in Python Certification Bundle. As the title suggests you...

While the hacker-sim genre tends to hide in the shadows a little bit, there’s always that one game that gets more mainstream attention. For this genre,...

In this Quick Look we are going to be looking at The Ultimate Java Programming Bundle: Lifetime Access currently 98% off at ($29). This bundle covers everything...

In this Quick Look, we are going to look a The Computer Hacker Professional Certification Bundle. This bundle comprises of 5 courses aimed at prepping you...

Ethical hacking or penetration testing is a much needed and fastly growing industry. It is estimated that hacking accounts for over $1 billion in lost revenue...

Music, Voice and Sound interface kits: What you need to know. When it comes learning Unix and Linux systems and language, there are a lot of...

UK Fines Facebook over Cambridge Analytica Scandal. The UK has hit Facebook a fine of $645,000 for the Cambridge Analytica Scandal. It was revealed earlier this year...

Underwater gadgets and drones.There’s an unending mystery to the great deep, the majority of the ocean remains unexplored and as technology advances, more and more people...
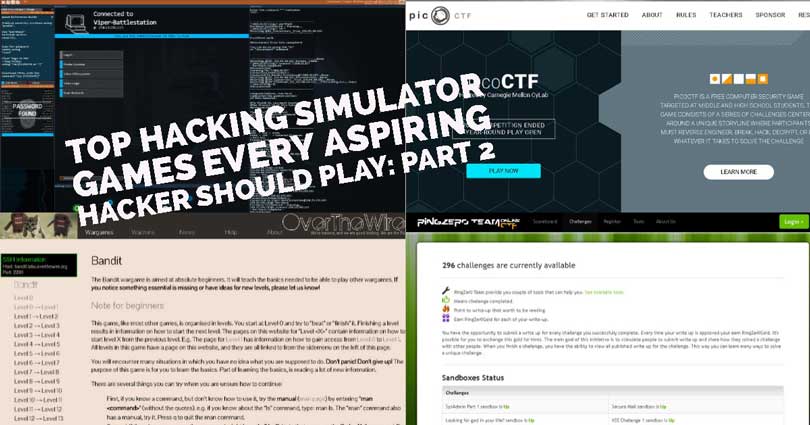
Top Hacking Simulator Games Every Aspiring Hacker Should Play: Part 2. Welcome back to our Top Hacking Simulator Games Every Hacker Should Play. For part two we’ll...