
Creating a Hidden Service via Tor for Beginners. How to create the hidden service? Download Tor first, that is a priority. You will also have to install...


Best Hacking Tools Of 2017 For Windows Finding the right hacking tools can be a challenge though, which is why we are here to ensure that...
![How to set up Linux Encrypted Networking Tool Secure Shell [SSH] in few easy steps on Ubuntu](https://d23vnjd1yg7tth.cloudfront.net/wp-content/uploads/2017/08/image_thumb-1.png)
How to set up Linux Encrypted Networking Tool Secure Shell [SSH] in few easy steps on Ubuntu Firstly, what is Secure Shell (SSH)? It is also...

How To Avoid SQL Injection Attacks In many ways, the popularity of programming languages such as PHP in web development are to blame for the prevalence...


Help my website has been hacked!prevention methods But when you get hacked, you don’t have to only repair the damaged file. You will also have to...
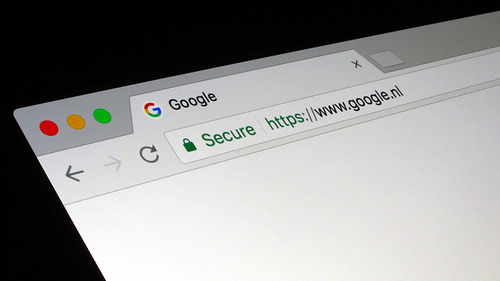
But what does that mean and how can we feel safer when you see that particular lock? When you see that lock, you will know that...

Cyber security is not only about keeping computers and mobile devices safe, but it is also keeping people’s sensitive data and privacy protected and keeping the...
Top Websites To Learn Ethical Hacking in 2017. What skills are required for Ethical Hacker? Some of the skills that are needed to become a white...


Have you heard the term GodMode before? May be you’ve played video games in god mode? In other words, a cheat code that makes you invincible....