

50 Million accounts exposed after Facebook security breach. Facebook has revealed that almost 50 million of its users accounts were left exposed due to a security...

There are dozens of digital marketing techniques used to showcase brands and products, each with its own set of best practices. Learning these skills is vital...


Teen who hacked Apple gets no Jail Time. Responsible for downloading 90GB of secure files, the teen has escaped jail time. At the time of the...


Google’s Project Zero has discovered a major Linux kernel vulnerability. This vulnerability exists for kernel versions 3.16 through to 4.18.8, beginning in August 2014. Project Zero...


UEFI Rootkit attacks no longer theoretical after one has been discovered in the wild. ESET Cybersecurity researchers have discovered malware, named LoJax, capable of modifying a...


The latest in funding and Recognition for Cyber Start-ups. When it comes to startups, a good idea and business plan will only get you so far,...
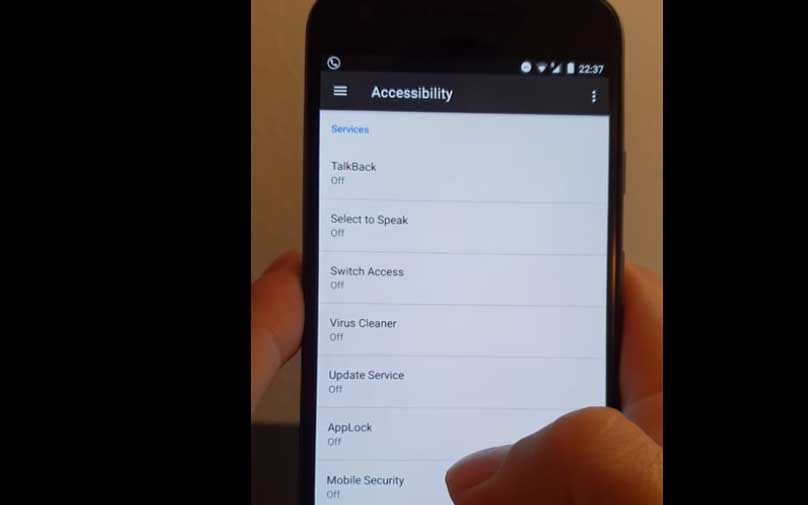

Banking Trojan found hidden in apps on the Google Play Store. The Android operating system makes up 76.82% of the mobile operating system market share worldwide....

The first computers ever created featured meager storage capacities that barely exceeded one megabyte. We’ve come a long way since then; on an individual scale, we...


Dangerous Linux Vulnerability is discovered by security researchers. An integer overflow occurs when an arithmetic operation creates a numeric value that is outside the typical range...

Professional certifications are certainly important in the world of the ethical hacker or penetration tester, but never underestimate the importance of personal development and undertaking niche...