
Kali Linux tips to consider after installation. With that in mind, here are some of the best things you can do to optimize it after its installation....

The Cyber Security FUD Problem. The FUD thing has been used by sales team in various industries for years. Fear, uncertainty, and doubt [ FUD] as...

Top Youtube channels to Learn Ethical Hacking in 2017. So, you decided to become an ethical hacker and looking for free resources online? There are many...


Great youtube channels to follow in Computer science tutorials. Some interesting youtube channels to follow to get started in computer science. Khan Academy >_ link CS50 >_link...

The idea is that dual booting can make things a reality here, so it’s up to you to make the right pick and opt for the...
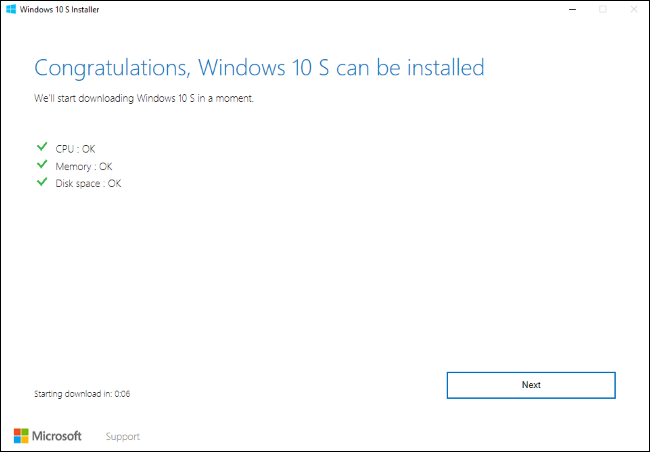

Windows 10 S is a new Windows variant designed to bring in front a dedicated set of features for some specific Windows devices. You can install...

Creating a Hidden Service via Tor for Beginners. How to create the hidden service? Download Tor first, that is a priority. You will also have to install...


Best Hacking Tools Of 2017 For Windows Finding the right hacking tools can be a challenge though, which is why we are here to ensure that...
![How to set up Linux Encrypted Networking Tool Secure Shell [SSH] in few easy steps on Ubuntu](https://d23vnjd1yg7tth.cloudfront.net/wp-content/uploads/2017/08/image_thumb-1.png)
How to set up Linux Encrypted Networking Tool Secure Shell [SSH] in few easy steps on Ubuntu Firstly, what is Secure Shell (SSH)? It is also...

Ever watch the “Ghost in the Shell” movie and think that wide scale hacking of machines, and huge networks are impossible? Now Japan, ranked number one...