

Liken to the “Me Too” viral campaign, corporations emerge from the dark to address the rising cyber-attacks.
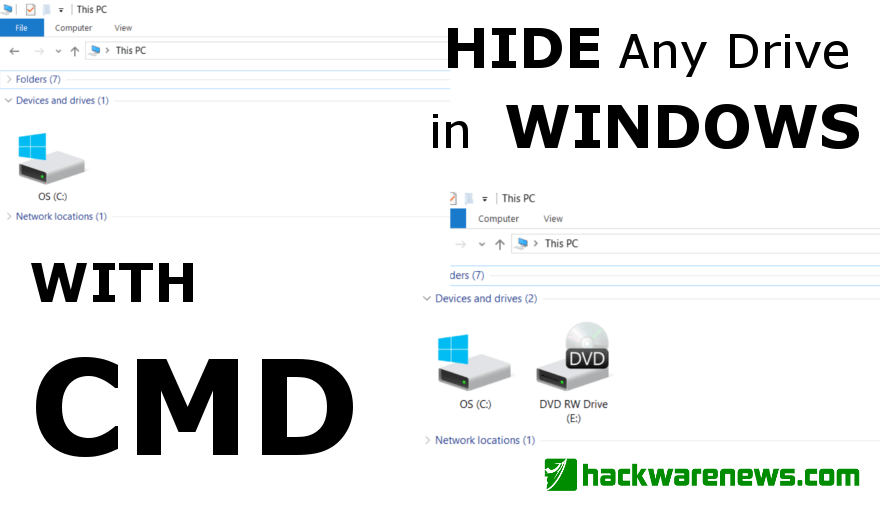
Hide Any Drive in Windows Using Command Prompt. Windows CMD is powerful tool to achieve some tasks that normally cannot be done without a third-party software/tools....

To Centurion Information Security, cybersecurity always come first. The Singapore-based penetration testing firm met up with HackwareNews team to share their experience on the ever-changing cyber-security...


Horangi has gotten a nod from venture firms and receives USD 3.1 million in return.

2018 is not going to be hack-free, so make your New Year Resolution here with "to-do lists” from Hackwarenews!

Google search in Linux CLI. Making a google search in Linux via CLI is not a just a geek thing anymore, as Linux gaining popularity among normal...

What are Top 10 Common Hacking Techniques? We don’t need to explain why it is important to know what are the commonly used hacking techniques. Below is...


Cryptocurrency such as Bitcoin, Etherum, Ripple have all suddenly became the darlings of financial investors. With its popularity and profitability, the cryptocurrency market also attracted unwanted...

Car-transportation application, Uber has fell victim to a cyber-attack that resulted data breach of around 57 million riders and paid a handsome fee to cover up...

Top 10 Linux Distro for Ethical Hacking and Penetration Testing. If you are pursuing a careers in infosec or working professionally in cyber security, surely you...