

Powerful Android Spyware Can Record Almost Anything On Infected Devices. Cybercriminals are turning legitimate apps into intrusive and sophisticated spyware, armed with extensive surveillance capabilities that...


New RCE Flaw in Apache Struts Could Be Another Equifax in the Making. Hackers are constantly on the lookout for system vulnerabilities that could give them...
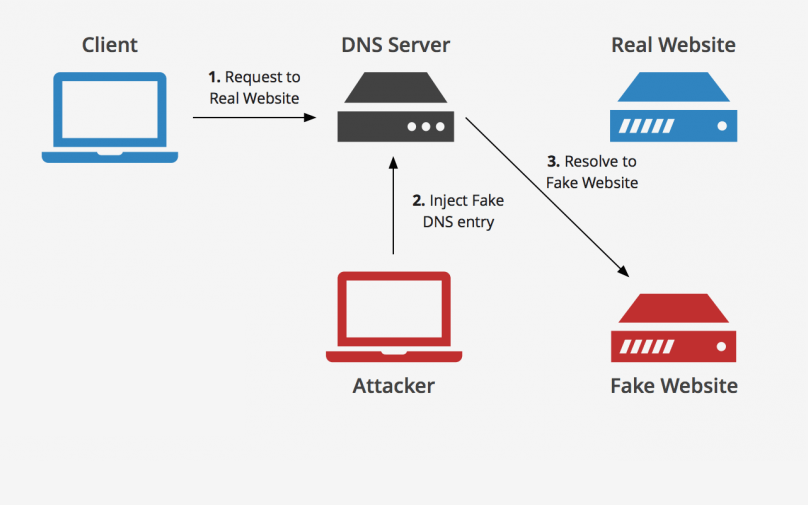

Dangers of DNS Interception. The Domain Name System is basically the internet’s phone book or yellow pages that translates domain name URLs into their equivalent numeric...


Users Say “Doh sveedahneeyah” to Their Instagram Accounts. It seems that Facebook and election machines aren’t the only things the Russians are busy with. They’re also...


Apple Gets Hacked from Down Under Their Noses–by a Kid. Apple is faced with an embarrassing situation. About 90GB worth of company data was stolen from their...

WhatsApp vulnerability allows users to easily spread fake news. WhatsApp, the hugely popular Facebook-owner messaging application, has recently come under scrutiny as multiple vulnerabilities have been...

Snapchat Hack – Giant Social Media Platform Source Code Leaked and Posted to GitHub. The source code of the social media giant app Snapchat recently appeared...

Ransomware attack: Alaska town returns to typewriters for a week. What do you when a cyber-attack cripples your computer network? You may just use an old-fashioned...

Reddit suffers major ‘security breach’ and hacker gained access to Reddit’s internal systems, despite SMS Two-Factor Authentication on employee accounts. Reddit discovered on 19 June 2018...

Ransomware hits shipping lines again. Chinese shipping firm, COSCO came under a ransomware attack that disrupted its system network in the United States (US). The attack took...