Cryptocurrency
Rebranded Vechain Thor seals ties with DNV GL, BMW and Oxford

Rebranded Vechain Thor seals ties with DNV GL, BMW and Oxford. Luxury car buyers now have another option of payment via cryptocurrency especially in the form of rebranded VeChain Thor.
Initially known as VeChain, the platform has since rebranded into VeChain Thor to facilitate large-scale enterprise (B2B) adoption with a new consensus mechanism. Moreover, the rebranding envisions to create an anti-counterfeit business ecosystem that enables transparent information flow, efficient collaboration and high-speed value transferring.
“As one of the world’s earliest blockchain technology companies, our platform has been successfully implemented for real-world applications for a wide array of industries,” said Sunny Lu, CEO of Shanghai-headquartered VeChain on the launch of VeChain Thor at Monday, 26 February 2018.
In Lu’s opinion, the biggest hurdles for the Blockchain does not lie with the technology but rather on the real applications with real value. Thus, the cryptocurrency has to be adopted by various industries such as pharmaceuticals, liquor, auto, agriculture, luxury goods, logistics and cold storage.
Under VeChain Thor, a two-coin system will be introduced which allows VeChain tokens to generate Thor Power (THOR) or a smart currency used to execute smart contracts and transactions on the platform.
Then, the VeChain tokens will be used as quick payment as currency to run business activities on the blockchain. People who hold more VeChain (VET) tokens will be given higher priority and rights on the VeChain Thor blockchain.
“In VeChain, we believe application use guides products, and the products guide technology,” explained Lu.
Thus, VeChain has been active in forming industrial partnership such as with German carmaker, BMW as well as academic institution like Oxford University as part of the VeResearch project for the development of VeChain Thor platform. The company also makes footprints in South Korea through cryptocurrency exchange named Coinnest, where it had been added into the trading platform.
One of the latest partners that liaises with VeChain belongs to the global assurance services provider DNV GL. The partnership ensures the more transparency of product and supplier information in tracking transactions using blockchain technology.
“In DNV GL, our main business is to provide trust and confidence and similarly our partnership with VeChain is to provided trust and confidence via the use of Blockchain technology.” said Luca Crisciotti, CEO of DNV GL – Business Assurance.
Overall, VeChain Thor holders can buy a wide variety of goods, not limited to BMW cars and the tokens did not hide transaction history as traditional purchasing currency and allow tracing of product through the supply chain.

BREAKING NEWS
Japanese Crypto-Robbery

Japanese Crypto-Robbery. Another crypto-currency raid happened in Japan leading to the perpetrators getting away with about 60 million dollars-worth of cryptocurrency.
Within two hours, Japanese cryptocurrency exchange Tech Bureau Corp. was hacked last September 14 which was unfortunately discovered four days after the culprits managed to steal 6.7 billion yen or 59.67 million dollars-worth of cryptocurrency composed of Bitcoin, Bitcoin Cash and Monacoin; more than half of which belonged to customers.
The cryptocurrency was stolen from internet-connected “hot wallets” which are more vulnerable than cold wallets that remain in the dark until connected.
The customers won’t have to wallow in despair though. Tech Bureau managed to merge with JASDAQ-listed Fisco Ltd. For a majority ownership investment amounting 5 billion yen in order to pay back the customers.
This comes after another massive cryptocurrency hack last January when crypto-exchange Coincheck lost a massive 530 million dollars-worth of digital currency. Coincheck in turn was absorbed by Japanese online brokerage group Monex Group Inc.
Amazing how resilient the industry remains, hack after hack. Despite these, over 160 entities express their willingness to enter the cryptocurrency exchange market, perhaps due to the recent Bitcoin surge. Bitcoin has since dropped but value remains at over 6,000 dollars.
Japanese crypto-exchanges have lately come under fire for lack of security and mismanagement, and will continue to burn more after the recent hack of Tech Bureau. The Japan Financial Services Agency has yet to approve the aforementioned cryptocurrency exchange applicants.
The FSA conducted an investigation and audit of various cryptocurrency exchanges and found that security was lax and management was sloppy. Apparently Tech Bureau hasn’t learned its lesson.
Further measures will be required to tighten security amidst Japan’s cryptocurrency regulation, the first country to do so. Regulation is seen by some as a threat to the openness and freedom of cryptocurrency much like the fledgling internet before censorship. But Japan sees it as more of an encouragement and a way to include much needed security measures much like cryptocurrency’s physical counterpart.
Photo by Ryo Yoshitake on Unsplash
[stackCommerce layout=”2″ count=”5″ sort=”best_sellers”][/stackCommerce]
Cryptocurrency
Cryptocurrency Exchanges Under Attack by Lazarus Through AppleJeus Malware

Cryptocurrency Exchanges Under Attack by Lazarus Through AppleJeus Malware. It’s been recently discovered that the Lazarus Group, an infamous North Korean cyber crime ring (supposedly backed by the government), has been targeting cryptocurrency exchanges, fintech companies and even banks with aggressive attacks involving high-value thefts.
Reports from Kaspersky Lab’s Global Research and Analysis Team have indicated that Lazarus have infiltrated an Asian cryptocurrency exchange, and are using Trojanized software to steal cryptocurrency. Specifically, they’ve been employing a macOS malware known as AppleJeus.
Vulnerability of macOS users
This is the first time the notorious Lazarus Group have been found to target macOS users, who traditionally fall victims to cyber attacks less often than their Windows counterparts. It’s believed that copies of the malware are being downloaded from what seems to be the website of a company who develops cryptocurrency trading software, which otherwise appears to be legitimate from the outset. However, after further investigation researchers have been unable to associate or verify it with a legitimate organization, raising serious questions about its validity.
The malware essentially gathers confidential information and details on the host computer, before sending it back to the command and control server. If the attacker deems it worth pursuing, they prompt for an update which installs Fallchill, a Trojan which provides almost unlimited access to the device, allowing information and data theft. From the user’s perspective, it simply seems like a standard software update.
Serious warnings are being issued
Kaspersky Lab seriously advises businesses and individuals like to not trust code simply based on digital certifications, a seemingly valid company profile and a genuine looking website – because these can still shield a malicious group seeking to cause serious damage through their attacks.
Businesses in particular are recommended to employ comprehensive and advanced security solutions to protect their networks and infrastructure, and to use multi-factor authentication for significant financial transactions.
Cryptocurrency
BitTorrent Software Update Hijacked 400,000 – PCs Last Week – Trojanized
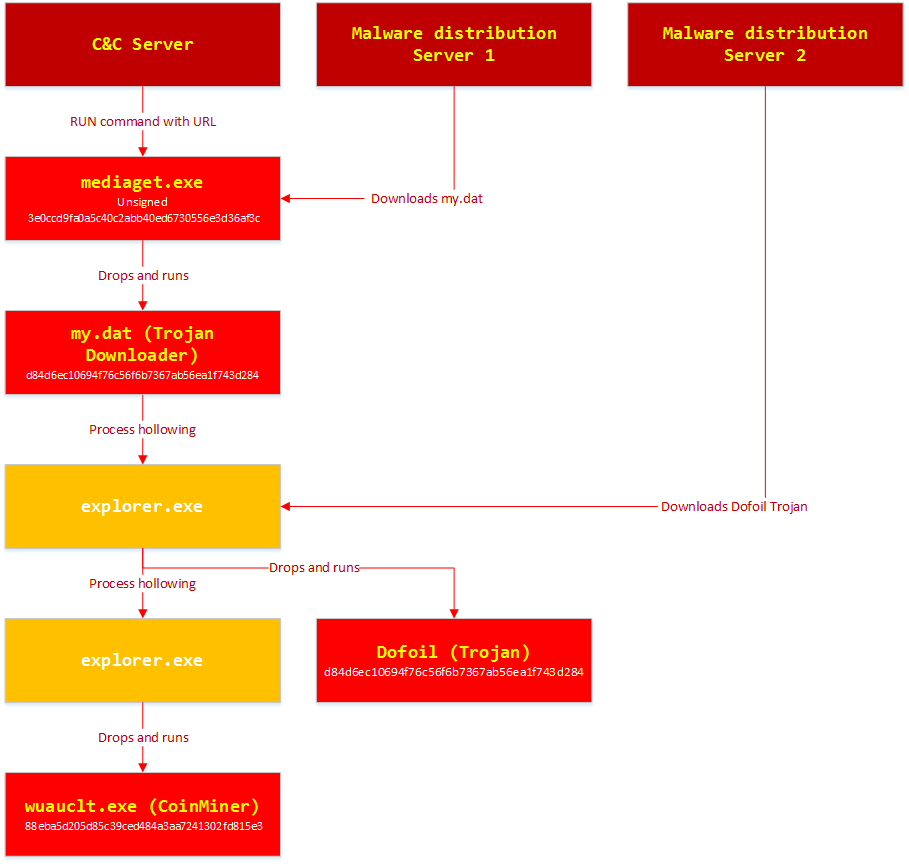
BitTorrent Software Update Hijacked 400,000 – PCs Last Week – Trojanized. A substantial malware uprising last week that spread the cryptocurrency mining malware to 400,000 computers within few hours was due to a backdoor of the BitTorrent names MediaGet. Also known as Dufoil or Smoke Loader, it works by dropping a cryptocurrency miner software as a payload on infected Windows machines and as a result that mine Electroneum (digital coins) by using CPU cycles.
The Smoke Loader campaign was uncovered by Microsoft Windows Defender R&D team that affected computers in Ukraine, Russia and Turkey. Defender team blocked the campaign before any severe damage could be done.
It took about 12 hours to spread the malware to a huge audience and it was not mentioned by Microsoft how this happened.
Few days back, once investigation took place Microsoft disclosed that the attack was targeted to update mechanism of MediGet software and pushed the trojanized software to users.
“A signed mediaget.exe downloads an update.exe program and runs it on the machine to install a new mediaget.exe. The new mediaget.exe program has the same functionality as the original but with additional backdoor capability,” the researchers team explain in a article post published on 14 March”
BitTorrent Software Update Hijacked 400,000 – PCs Last Week – Trojanized
-
 GAME REVIEW7 years ago
GAME REVIEW7 years agoTop Hacking Simulator Games Every Aspiring Hacker Should Play: Part 1
-

 DEALS7 years ago
DEALS7 years agoGreat Ethical Hacking Courses for Beginners
-

 HACKING NEWS7 years ago
HACKING NEWS7 years agoThe APT attacks hitting East Asia
-

 GAME REVIEW7 years ago
GAME REVIEW7 years agoHacknet Review
-

 BREAKING NEWS7 years ago
BREAKING NEWS7 years agoUS Online Retail Company suffered a data breach affecting 6.5 million customers
-

 BREAKING NEWS7 years ago
BREAKING NEWS7 years agoUK Fines Facebook over Cambridge Analytica Scandal
-

 HOW TO7 years ago
HOW TO7 years agoHow To Become an Ethical Hacker – Beginners Guide
-

 DEALS7 years ago
DEALS7 years agoMusic, Voice and Sound interface kits: What you need to know